HowTo:Infect your computer with Malware
Are you tired of that dull computer you have used for the last four years? Ever wanted to just "Trash it"? Don't fret. Because by the end of reading this entry, your computer will be infected in no time!
Getting Started[edit]
First off, make sure your Operating System is relatively recent, oh, and for the best results, use Windows Vista. You do not want to be using an OS that is over 10 years old, because Malware designed for those Operating Systems are pretty much extinct nowadays (much like the cruddy 1999 Maldal Windows Worm that infected Windows9x Operating Systems back in the day).
If you have your computer already, that is fantastic! If you are yet to grip your filthy hands onto one of Bill Gates zappy inventions, consider the following.
The Infection Procedure[edit]
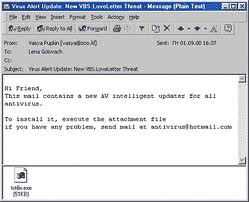
And now for the fun part, infecting the system. To do this, simply try searching websites with inappropriate URLs (Example: RedTube.com Childrenslaughter.com, "Children" and "Slaughter", get it?). Also, if you happen to sight a pop-up advertisement containing something along the lines of, "U R TEH 5,643,681,602,366,439,684 VIZITOOR 2 DIS WEBSHITE, CLIK HEER 2 CLAM UR PR1SE!!!!!!!!!!!!!!!111", you should probably understand that they are in fact offering you a delightful treat, so scroll your cursor over the advertisement and click on it. Chances are, a Trojan Horse such as WIN32.Flame@mm might arrive bundled onto your Desktop. An alternate method is to browse the spam folder on your computer, and click on any attachments you might find in an email marked as spam. Be sure to scan it with a virus scanner, since you do not want a virus on your computer, but rather, malware. Or, if you want both, click away on all the popup banners you find and all the attachments in your spam box (without scanning after download), and you will surely get a delightful present, along with more popup banners.
The final conduct[edit]
Finally, once a suspicious looking file (in most cases, an Executable file) arrives on your Desktop, go ahead and double-click on it to screw your computer up. If you wish, you can continue to watch your C:\Windows file get overwritten in the process, but that is optional. Once you find out that switching the computer ON gives a DOS Command Prompt screen instead of a traditional Desktop, you can then decide on what Operating System you would like to install (we personally recommend using MS-DOS).

|
HowTo This article is part of Uncyclopedia's HowTo series. See more HowTos |